ASTUTE complements existing tools, including SIEM and UBA, to provide enhanced visibility into your organization’s blind spots.
ASTUTE can...
ASTUTE is a security data analytics platform, enabling security teams and business partners with timely, actionable alerts and intelligence.
ASTUTE moves as fast as you. With a variety of deployment models including on-premises, hybrid, or fully cloud-based, clients measure ROI in weeks, not months.
ASTUTE makes security a team sport. Leveraging advanced machine learning and workflow optimization, ASTUTE ensures that the right information is making it to the right people every time.
ASTUTE loves data challengesHere's how we're helping clients
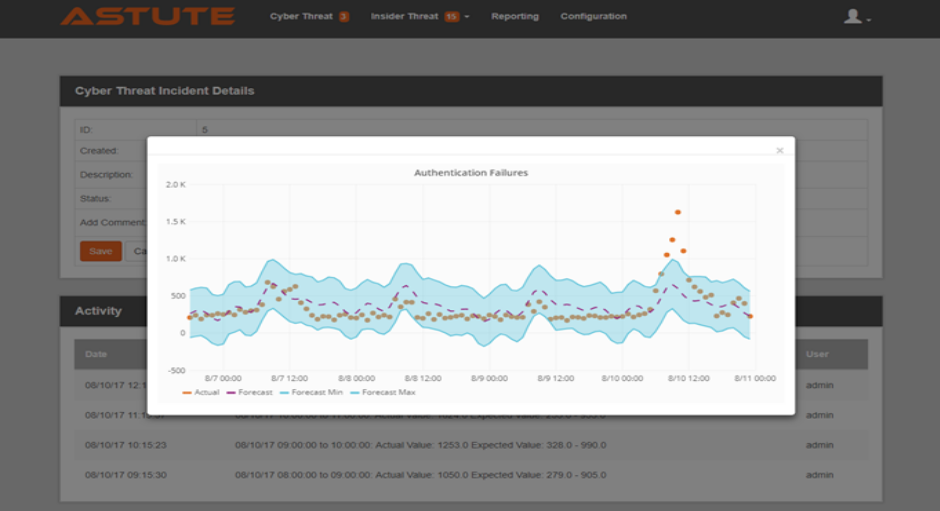
Anomaly Detection
As attack tactics and techniques constantly evolve, anomaly detection provides early warning of atypical activities in the environment. Leveraging advanced machine learning techniques, ASTUTE constantly monitors the environment and escalates anomalies to the right teams for investigation.
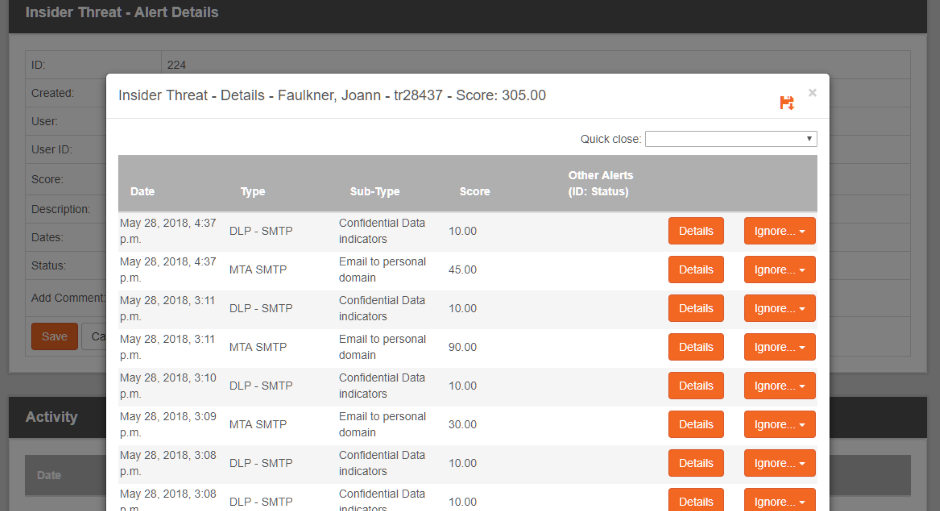
Insider Threat
Existing security tools deployed in the enterprise provide small pieces of the insider threat puzzle. Without the ability to aggregate these activities and correlate them with identities, most go unnoticed. ASTUTE assembles these pieces, aggregating seemingly benign events into a comprehensive risk picture of employees and contractors.
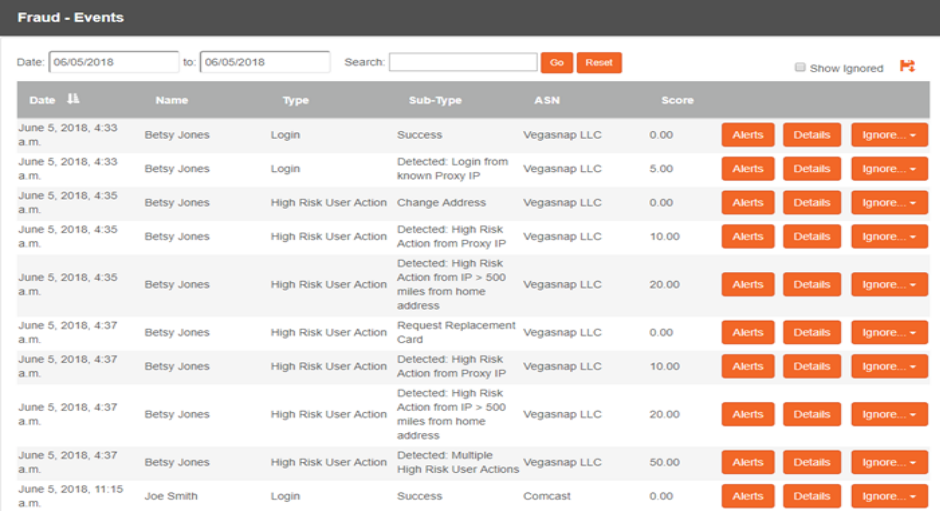
User Activity Reviews
Drowning in Data Loss Prevention alerts? Or a mountain of Database Activity Monitoring data? Astute aggregates and scores events from one or more systems and escalates high-risk behavior for review. Similar to User Access Review processes, high-risk activity is escalated to Managers or System Owners for review – minimizing manual investigation by security operations teams and engaging others in the security fight.